How to Develop Insider Risk Policies for Project Teams in 6 Actionable Steps
Are you struggling to develop project insider risk policies for your teams?
As a life coach, I’ve helped many professionals navigate these challenges in insider threat prevention. I understand how difficult it can be to find practical use cases and examples for project team security protocols.
In this article, you’ll discover specific strategies and actionable steps to tailor insider risk policies to your project scenarios and team structures. We’ll explore risk assessment for project teams and insider risk mitigation strategies.
Let’s dive into developing project insider risk policies.

Understanding the Challenges of Insider Risk Policies
Creating tailored insider risk policies can be a daunting task for project managers. Many clients initially struggle to identify specific risks and develop practical policies that address them when developing project insider risk policies.
This lack of clarity often leads to vulnerabilities in project security and challenges in implementing effective insider threat prevention measures.
I often see clients benefit from structured approaches, yet the difficulty lies in finding relatable, real-world examples. Without these, it’s challenging to craft policies that resonate with their unique project needs and establish robust project team security protocols.
Moreover, project managers frequently face the challenge of balancing strict security measures with team productivity. Overly restrictive policies can hinder progress, while lax policies leave gaps for potential threats, making it crucial to implement appropriate data access controls in project management.
The pain of these challenges is real. Many project managers feel overwhelmed, unsure of where to start, and fearful of missing critical risks when developing project insider risk policies.
This is where a systematic approach can make all the difference in creating effective insider risk mitigation strategies.

Key Steps to Developing Insider Risk Policies for Project Teams
Overcoming this challenge requires a few key steps when developing project insider risk policies. Here are the main areas to focus on to make progress:
- Conduct a Project-Specific Risk Assessment: Identify and evaluate insider risks specific to your project, focusing on risk assessment for project teams.
- Create Clear Access Control Policies for Teams: Define roles and implement role-based access controls, addressing data access controls in project management.
- Implement Regular Security Awareness Training: Schedule and conduct engaging information security training for project staff.
- Establish Incident Reporting Procedures: Design and assign clear incident reporting protocols as part of insider threat prevention strategies.
- Define Data Handling Guidelines for Projects: Create comprehensive guidelines for data management, incorporating cybersecurity best practices for project teams.
- Set Up Continuous Monitoring of Team Activities: Utilize tools to track and detect unusual behavior, implementing employee monitoring in project environments.
Let’s dive in!
1: Conduct a project-specific risk assessment
Conducting a project-specific risk assessment is crucial for identifying and mitigating potential insider threats when developing project insider risk policies.
Actionable Steps:
- Identify and document potential insider risks: List all possible risks that could impact your project, focusing on those specific to your team and operations, including cybersecurity best practices for project teams.
- Evaluate the likelihood and impact of each risk: Use risk assessment tools to gauge the probability and potential impact of each identified risk, considering insider threat prevention measures.
- Prioritize risks based on impact: Rank the risks in order of their potential impact on your project, focusing on the most critical ones first to develop effective project team security protocols.
Key benefits of conducting a thorough risk assessment for project teams:
- Enhances project security
- Optimizes resource allocation
- Improves decision-making
Explanation: These steps help ensure you address the most significant risks to your project. By prioritizing high-impact risks, you can allocate resources effectively and implement insider risk mitigation strategies.
For more information on risk assessment tools, check out this resource from CERT Insider Threat.
Remember, a thorough risk assessment lays the foundation for effective insider risk policies, including data access controls in project management and compliance and insider risk management.

2: Create clear access control policies for teams
Creating clear access control policies for teams is vital to ensure sensitive information is protected when developing project insider risk policies.
Actionable Steps:
- Define roles and responsibilities: Clearly outline each team member’s access levels based on their role and responsibilities, incorporating cybersecurity best practices for project teams.
- Implement role-based access controls: Use role-based access controls to restrict access to sensitive data, ensuring only authorized personnel have access, which is crucial for insider threat prevention.
- Regularly review and update access permissions: Conduct periodic reviews to update access permissions as team members’ roles evolve, aligning with project team security protocols.
Explanation: These steps help maintain a secure environment by limiting access to sensitive information. Role-based access controls are crucial for minimizing security risks and implementing effective data access controls in project management.
Regular updates ensure that access permissions are current and relevant. For more detailed guidelines on implementing access controls, check out this resource from Microsoft Purview.
Clear access control policies create a balanced approach to security and productivity, supporting insider risk mitigation strategies in project environments.

3: Implement regular security awareness training
Implementing regular security awareness training is crucial to ensure your team remains vigilant and informed about potential threats when developing project insider risk policies.
Actionable Steps:
- Schedule monthly security training sessions: Arrange regular training sessions to keep security knowledge fresh and up-to-date, focusing on insider threat prevention and project team security protocols.
- Develop engaging training materials: Use real-life examples and interactive content to make training sessions more effective and memorable, covering topics like confidentiality agreements for team members and data access controls in project management.
- Conduct periodic assessments: Regularly test and measure the effectiveness of your training programs to identify areas for improvement in risk assessment for project teams and employee monitoring in project environments.
Explanation: These steps help maintain a high level of security awareness and readiness among your team.
Regular training ensures that team members are well-equipped to recognize and respond to potential threats. For more about effective training programs, see Insider Threat Mitigation resources.
Regular security training fosters a culture of vigilance and proactive risk management, essential for implementing effective insider risk mitigation strategies and maintaining compliance in insider risk management.

4: Establish incident reporting procedures
Establishing incident reporting procedures is crucial to ensure prompt and efficient responses to potential insider threats when developing project insider risk policies.
Actionable Steps:
- Design a clear incident reporting protocol: Create a straightforward process for reporting incidents that all team members can follow, aligning with project team security protocols.
- Assign specific roles for handling reports: Identify individuals responsible for managing and responding to reported incidents as part of your insider risk mitigation strategies.
- Conduct mock reporting exercises: Regularly practice incident reporting to ensure team members are prepared and protocols are effective, enhancing cybersecurity best practices for project teams.
Key components of an effective incident reporting system:
- User-friendly reporting channels
- Clear escalation procedures
- Confidentiality measures aligned with confidentiality agreements for team members
Explanation: These steps are vital for maintaining project security by ensuring quick and efficient responses to potential threats, supporting insider threat prevention efforts.
Clear protocols and assigned roles streamline the reporting process, while mock exercises improve readiness and support information security training for project staff.
For more insights, check out Insider Threat Mitigation resources.
Effective incident reporting procedures enhance your team’s ability to address and mitigate insider threats promptly, strengthening overall compliance and insider risk management in project environments.

5: Define data handling guidelines for projects
Defining data handling guidelines is crucial for developing project insider risk policies and securing sensitive information within your project teams.
Actionable Steps:
- Create comprehensive data classification guidelines: Establish clear criteria for classifying data based on sensitivity and importance, aligning with insider threat prevention strategies.
- Implement secure data storage solutions: Use encrypted storage methods to protect sensitive data from unauthorized access, reinforcing project team security protocols.
- Enforce secure data sharing practices: Ensure that data sharing within the team follows strict encryption and data access controls in project management.
Explanation: These steps help safeguard your project’s sensitive information by ensuring proper data management and insider risk mitigation strategies.
Properly classified and securely stored data reduces the risk of accidental leaks or breaches, supporting cybersecurity best practices for project teams.
For further guidance, see Microsoft Purview on insider risk management.
By defining clear data handling guidelines, you enhance your project’s overall security posture and support compliance and insider risk management efforts.

6: Set up continuous monitoring of team activities
Continuous monitoring of team activities is essential for detecting and mitigating insider threats promptly when developing project insider risk policies.
Actionable Steps:
- Utilize monitoring tools: Deploy tools to track team activities and detect unusual behavior patterns, enhancing project team security protocols.
- Establish alerts for high-risk actions: Set up alerts for actions that indicate potential threats, such as unauthorized data access, as part of your insider risk mitigation strategies.
- Conduct regular audits: Regularly review monitoring logs and conduct audits to identify potential risks and ensure compliance in insider risk management.
Essential elements of an effective monitoring system for project teams:
- Real-time activity tracking
- Anomaly detection algorithms
- Customizable alert thresholds
Explanation: These steps help maintain a proactive stance in identifying and addressing insider threats in project environments.
Continuous monitoring ensures that any suspicious activities are detected early, allowing for timely intervention and supporting cybersecurity best practices for project teams.
For more insights on setting up monitoring tools, visit Microsoft Purview on insider risk management.
Taking these measures enhances your project’s security and minimizes the risk of insider threats when developing project insider risk policies.

Partner with Alleo for Effective Insider Risk Policies
We’ve explored the challenges of developing project insider risk policies for project teams. Did you know you can work directly with Alleo to make this journey easier and faster?
Setting up an account is simple and quick. Alleo helps you create a personalized plan tailored to your project needs, including insider threat prevention strategies.
The AI coach provides full coaching sessions on project team security protocols, just like a human coach.
Alleo assists in conducting project-specific risk assessments for project teams using templates and tracking progress. Schedule and remind team members about information security training sessions for project staff.
Track their completion effortlessly, ensuring compliance and insider risk management.
Document and automate incident reporting procedures, ensuring timely and efficient responses. Implement data access controls in project management and continuously monitor team activities with Alleo’s customizable workflows and reminders.
Alleo follows up on your progress, handles changes, and keeps you accountable via text and push notifications, supporting your insider risk mitigation strategies.
Ready to get started for free? Let me show you how to enhance your project team’s cybersecurity best practices!
Step 1: Log In or Create Your Account
To begin developing insider risk policies with Alleo’s AI coach, simply log in to your account or create a new one to access personalized guidance tailored to your project team’s security needs.

Step 2: Choose “Building better habits and routines”
Select “Building better habits and routines” to establish consistent practices that will strengthen your insider risk management, helping you create and maintain effective policies for your project teams.

Step 3: Selecting the life area you want to focus on
Choose “Career” as your focus area to address insider risk policies effectively, as this directly impacts your project management skills and team security practices.

Step 4: Starting a coaching session
Begin your journey with Alleo by scheduling an initial intake session, where you’ll work with the AI coach to assess your project’s insider risk challenges and create a personalized action plan for developing effective policies.

Step 5: Viewing and managing goals after the session
After your coaching session on insider risk policies, check the app’s home page to view and manage the goals you discussed, allowing you to track your progress in implementing effective security measures for your project team.
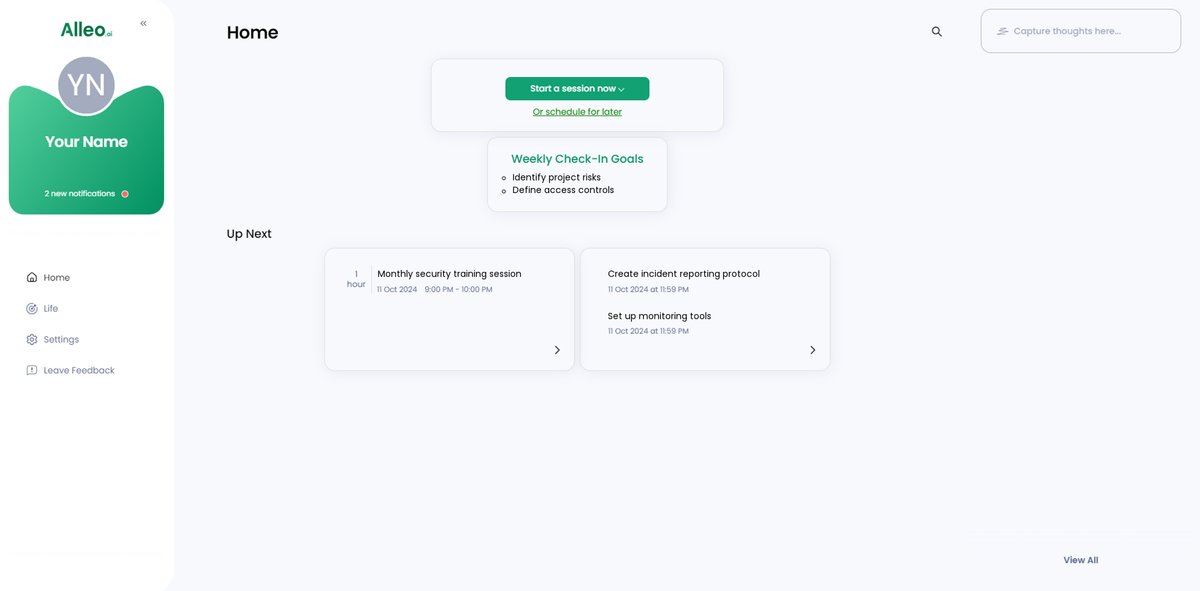
Step 6: Adding events to your calendar or app
Use Alleo’s calendar and task features to schedule security training sessions, set reminders for risk assessments, and track your progress in implementing insider risk policies, ensuring you stay on top of your project security goals.
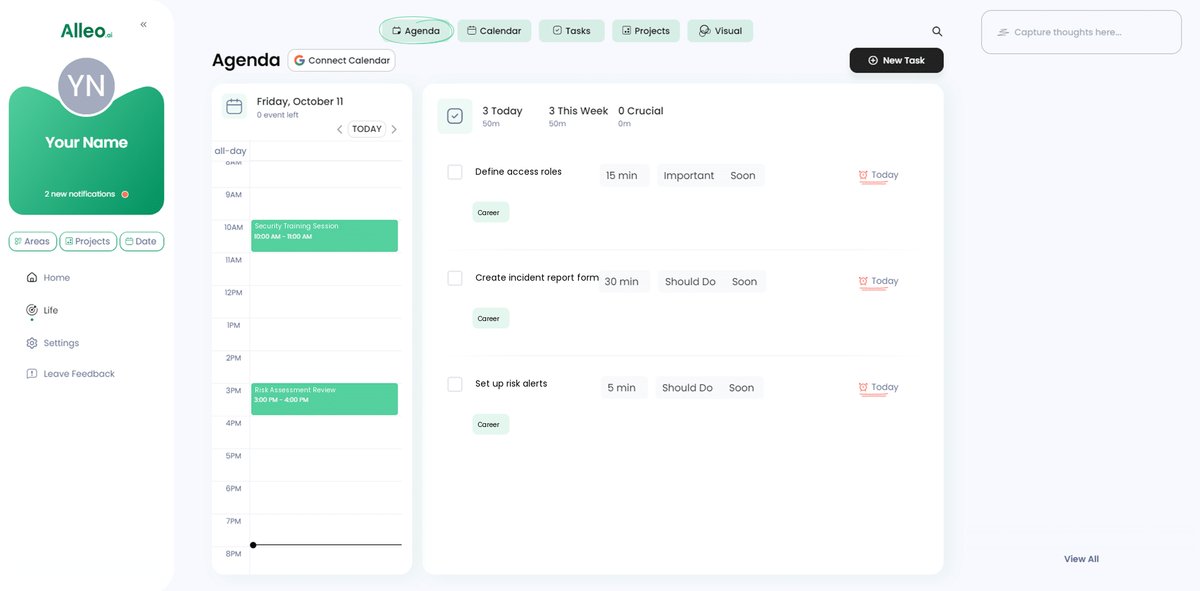
Wrapping Up Your Insider Risk Policies Journey
You’ve taken the first steps toward developing project insider risk policies and securing your projects with tailored strategies. It’s a challenging path, but one that’s crucial for your team’s success and insider threat prevention.
Remember, the key is a structured approach. Conducting risk assessments for project teams, implementing data access controls in project management, and regular information security training for project staff are fundamental.
Don’t forget to establish incident reporting, define data handling guidelines, and continuously monitor activities. Each of these steps is vital for effective insider risk mitigation strategies.
I know developing project insider risk policies isn’t easy, but you’re not alone. Alleo is here to help with cybersecurity best practices for project teams.
Start harnessing Alleo’s tools to streamline your risk management and enhance project team security protocols. You can begin this transformative journey for free.
Let’s make your projects secure and successful together while ensuring compliance and insider risk management.