7 Critical Strategies for IT Managers to Evaluate Workspace App Security Risks
Have you ever considered how much sensitive company data might be at risk due to poorly designed or malicious apps? Evaluating workspace app security risks is crucial in today’s digital landscape.
As a life coach, I’ve helped many professionals navigate these challenges. In my experience, the threat of cyber incidents has never been higher, especially in remote work environments where cybersecurity is paramount.
In this article, you’ll learn strategies to evaluate and mitigate the risks associated with Workspace Marketplace apps. We’ll cover practical steps and tools to protect your data, including IT security best practices and user access control for workspace applications.
Let’s dive into evaluating workspace app security risks and explore cloud-based workspace security measures.

Understanding the Risks of Malicious Apps in Your Workspace
When it comes to evaluating workspace app security risks, the challenges can be daunting. Many clients initially struggle with the extensive access permissions granted to apps, which can lead to significant data breaches. This is a crucial aspect of IT security best practices.
One common issue is the vulnerability of poorly designed apps. These apps can easily be exploited by cybercriminals, putting sensitive company data at risk. Regular workspace application vulnerability assessments are essential for cloud-based workspace security.
Several clients have reported discovering unauthorized access to their systems, often tracing it back to seemingly harmless apps. This can be particularly painful when dealing with sensitive financial information, highlighting the need for robust user access control for workspace applications.
In my experience, it’s crucial to recognize these risks early. By understanding the potential threats and taking proactive measures, you can protect your organization from significant data loss. This is especially important when evaluating workspace app security risks in remote work environments.
For example, regular vulnerability scans can identify weaknesses before they are exploited. This approach helps ensure your data remains secure and aids in compliance and regulatory considerations for IT managers.

A Roadmap to Secure Your Workspace Apps
Overcoming this challenge requires a few key steps. Here are the main areas to focus on when evaluating workspace app security risks and implementing IT security best practices:
- Conduct a comprehensive security risk assessment: Identify and categorize all workspace applications, assess risk profiles, and inform stakeholders about potential cybersecurity risks in remote work environments.
- Implement a 5×5 risk matrix for app evaluation: Train IT managers on risk management techniques, categorize apps based on their security level, and update the matrix regularly to ensure compliance and regulatory considerations for IT managers are met.
- Perform regular vulnerability scans on apps: Schedule monthly workspace application vulnerability assessments, use automated tools for cloud-based workspace security, and prioritize fixes.
- Establish clear app approval and vetting process: Develop a standardized process for evaluating workspace app security risks, use a vetting checklist for third-party app security evaluation, and maintain a whitelist.
- Train users on safe app installation practices: Conduct training sessions on mobile app security for enterprise, create guidelines for data protection in collaborative apps, and encourage reporting.
- Monitor app permissions and data access patterns: Implement monitoring tools for user access control in workspace applications, set up alerts, and review permissions regularly.
- Implement automated security testing for apps: Integrate testing into development processes, use analysis tools for evaluating workspace app security risks, and update protocols as needed.
Let’s dive in!
1: Conduct a comprehensive security risk assessment
Conducting a comprehensive security risk assessment is essential to safeguard your organization’s data and identify potential threats when evaluating workspace app security risks.
Actionable Steps:
- Identify all apps used: Make a detailed list of all apps currently in use within your organization, including cloud-based workspace security solutions.
- Assess risk profiles: Evaluate each app’s risk based on its access permissions and data sensitivity, considering mobile app security for enterprise.
- Develop a risk report: Create a risk assessment report to inform stakeholders about potential vulnerabilities and compliance considerations for IT managers.
Explanation: Conducting a thorough security risk assessment helps you understand where your vulnerabilities lie and take proactive steps to mitigate them, aligning with IT security best practices.
By identifying and categorizing all apps, you can better manage the risks they pose. Assessing each app’s risk profile allows you to prioritize your efforts where they are most needed, especially in remote work environments.
Finally, developing a risk assessment report ensures that all stakeholders are aware of the risks and can take appropriate action. For more information on this process, you can refer to this detailed guide.
These steps set the foundation for a robust app security strategy and workspace application vulnerability assessment. Let’s move on to the next part of our comprehensive approach.

2: Implement a 5×5 risk matrix for app evaluation
Implementing a 5×5 risk matrix is crucial for efficiently evaluating workspace app security risks and ensuring data protection in collaborative apps.
Actionable Steps:
- Train IT managers: Teach them how to use the 5×5 risk matrix for evaluating workspace app security risks. This ensures consistency and accuracy in risk management for IT managers.
- Apply the matrix: Use it to categorize apps based on their risk levels, from acceptable to unacceptable, as part of your workspace application vulnerability assessment.
- Regular updates: Continuously update the risk matrix with new data and insights from ongoing assessments to improve cloud-based workspace security.
Explanation: Implementing a 5×5 risk matrix allows you to objectively assess and categorize apps, making it easier to prioritize security efforts. This structured approach can help safeguard sensitive data and is essential for cybersecurity in remote work environments.
For more details on using a 5×5 risk matrix, check out this guide from SafetyCulture.
Key benefits of using a 5×5 risk matrix include:
- Standardized risk assessment across all apps, supporting IT security best practices
- Clear visualization of risk levels for mobile app security for enterprise
- Easier prioritization of security efforts and user access control for workspace applications
This step is a key part of creating a secure app environment and evaluating workspace app security risks.
Next, we’ll discuss the importance of regular vulnerability scans.

3: Perform regular vulnerability scans on apps
Conducting regular vulnerability scans on apps is essential to identify and mitigate security weaknesses before they can be exploited, a crucial step in evaluating workspace app security risks.
Actionable Steps:
- Schedule monthly scans: Set up monthly vulnerability scans for all installed apps to ensure consistent monitoring, adhering to IT security best practices.
- Utilize automated tools: Deploy automated tools to detect and report security weaknesses in real-time, enhancing efficiency in workspace application vulnerability assessment.
- Review and prioritize: Analyze scan results with your IT team and prioritize fixes for high-risk vulnerabilities, focusing on mobile app security for enterprise and cloud-based workspace security.
Explanation: Regular vulnerability scans help you stay ahead of potential threats by uncovering weaknesses early. This proactive approach ensures your data remains secure and minimizes the risk of breaches, supporting risk management for IT managers.
For more insights on the importance of vulnerability scans, check out this detailed guide.
By integrating these steps, you can greatly enhance your app security strategy and improve cybersecurity in remote work environments. Next, we’ll discuss establishing a clear app approval and vetting process.

4: Establish clear app approval and vetting process
Establishing a clear app approval and vetting process is crucial for evaluating workspace app security risks and safeguarding your organization’s sensitive data from risky apps.
Actionable Steps:
- Develop a standardized app approval process: Involve multiple stakeholders to ensure thorough evaluation and accountability in workspace application vulnerability assessment.
- Implement a vetting checklist: Evaluate apps before installation based on a set of predefined security criteria, aligning with IT security best practices.
- Maintain a whitelist of approved apps: Regularly review and update it to ensure ongoing relevance and security, especially for cloud-based workspace security.
Explanation: Implementing these steps helps minimize the risks associated with app installations by ensuring each app is rigorously assessed before use, which is crucial for data protection in collaborative apps.
This approach aligns with industry trends emphasizing proactive security measures and risk management for IT managers.
For instance, the AuditBoard highlights the importance of regular risk assessments in maintaining compliance and security.
By following these steps, you can significantly reduce the likelihood of data breaches and improve cybersecurity in remote work environments.
Next, we’ll discuss the importance of training users on safe app installation practices.

5: Train users on safe app installation practices
Incorporating safe app installation practices is vital for securing your organization’s sensitive data and evaluating workspace app security risks.
Actionable Steps:
- Conduct regular training sessions: Schedule frequent sessions to educate users on identifying and avoiding malicious apps, focusing on IT security best practices.
- Create clear guidelines: Develop easy-to-understand guidelines for safe app installation and usage, ensuring users follow best practices for workspace application vulnerability assessment.
- Encourage prompt reporting: Urge users to report any suspicious app behavior to the IT department immediately to mitigate risks in cloud-based workspace security.
Explanation: Training users on safe app installation practices helps prevent data breaches and ensures that everyone in the organization is vigilant about mobile app security for enterprise.
This proactive approach aligns with current industry trends emphasizing the importance of cybersecurity training. For further reading on this topic, refer to this comprehensive guide.
Key elements of effective user training include:
- Interactive workshops and simulations on evaluating workspace app security risks
- Regular updates on emerging threats in cybersecurity in remote work environments
- Clear communication channels for reporting concerns related to data protection in collaborative apps
By implementing these steps, you’ll create a more secure app environment and enhance overall data protection, addressing user access control for workspace applications and third-party app security evaluation.

6: Monitor app permissions and data access patterns
Monitoring app permissions and data access patterns is critical for maintaining the security of your sensitive company data and evaluating workspace app security risks.
Actionable Steps:
- Implement real-time monitoring tools: Deploy tools that monitor app permissions and data access in real-time to catch any unusual activities immediately, enhancing cybersecurity in remote work environments.
- Set up alerts for unauthorized access: Configure alerts to notify the IT team of any unauthorized or suspicious access patterns, enabling swift response and improving user access control for workspace applications.
- Periodically review permissions: Regularly review app permissions and data access levels, revoking any unnecessary or excessive permissions as part of IT security best practices.
Explanation: These steps ensure that you can quickly identify and respond to potential security threats when evaluating workspace app security risks. Real-time monitoring and alerts help you stay vigilant, while periodic reviews ensure your permissions remain up-to-date, supporting data protection in collaborative apps.
For more insights into continuous monitoring practices and their benefits, refer to FedRAMP’s guidelines.
By implementing these measures, you’ll strengthen your app security and reduce the risk of data breaches, addressing workspace application vulnerability assessment concerns.
Next, we’ll discuss incorporating automated security testing for apps.

7: Implement automated security testing for apps
Implementing automated security testing for apps is essential to identify vulnerabilities early and ensure continuous protection when evaluating workspace app security risks.
Actionable Steps:
- Integrate automated testing tools: Embed automated security testing tools into your app development and deployment pipeline to catch issues early, aligning with IT security best practices.
- Utilize both static and dynamic analysis: Use static analysis to examine code at rest and dynamic analysis to test running applications for comprehensive coverage, enhancing workspace application vulnerability assessment.
- Regularly update testing protocols: Continuously update your testing protocols to address emerging threats and vulnerabilities, crucial for cloud-based workspace security.
Explanation: These steps ensure a proactive defense against security threats. By integrating automated tools and utilizing both static and dynamic analyses, you can identify and mitigate vulnerabilities early, supporting risk management for IT managers.
Regular updates to testing protocols are crucial to stay ahead of new threats. For more insights into the importance of automated security testing, refer to this guide.
Automated security testing offers several advantages:
- Faster detection of vulnerabilities
- Consistent and repeatable testing processes
- Reduced human error in security assessments
By incorporating these measures, you can significantly enhance your app security strategy and improve cybersecurity in remote work environments.

Partner with Alleo to Secure Your Workspace Apps
We’ve explored the challenges of evaluating workspace app security risks and the steps to tackle them. But did you know Alleo can make this process easier and faster, helping you implement IT security best practices?
Setting up an account with Alleo is simple. Create a personalized security plan tailored to your needs, including workspace application vulnerability assessment and cloud-based workspace security measures.
Work with our AI coach to identify and address app vulnerabilities, enhancing your risk management for IT managers. Alleo will follow up on your progress, handle changes, and keep you accountable via text and push notifications, supporting cybersecurity in remote work environments.
Ready to get started for free and improve your approach to evaluating workspace app security risks?
Let me show you how!
Step 1: Logging in or Creating an Account
To begin securing your workspace apps with our AI coach, simply Log in to your account or create a new one if you haven’t already.

Step 2: Choose “Building better habits and routines”
Click on “Building better habits and routines” to focus on developing consistent app security practices, helping you establish a robust defense against potential workspace vulnerabilities and data breaches.

Step 3: Select “Career” as Your Focus Area
Choose “Career” as your focus area to address workplace app security challenges, aligning with the article’s emphasis on protecting sensitive company data and enhancing your professional cybersecurity practices.

Step 4: Starting a coaching session
Begin your journey with Alleo by scheduling an intake session, where our AI coach will help you create a personalized security plan for evaluating and securing your workspace apps.

Step 5: Viewing and managing goals after the session
After your coaching session, easily review and manage the app security goals you discussed by accessing them on the home page of the Alleo app, allowing you to track your progress and stay accountable in securing your workspace apps.
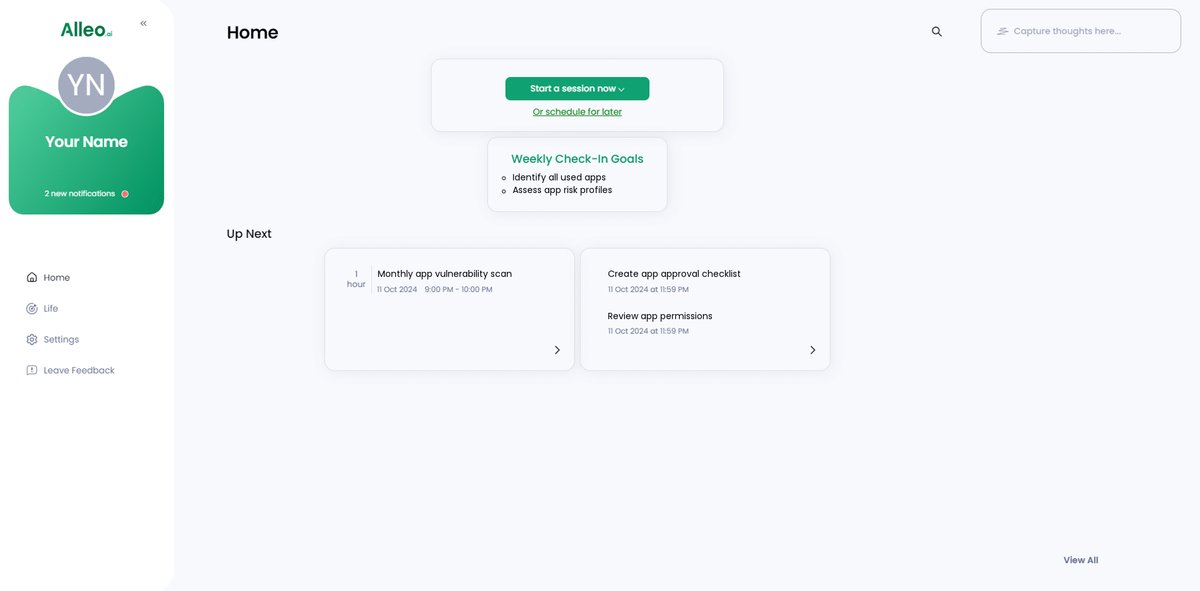
Step 6: Adding events to your calendar or app
Use the calendar and task features in Alleo to schedule and track your progress on implementing app security measures, allowing you to stay organized and accountable as you work towards a more secure workspace environment.
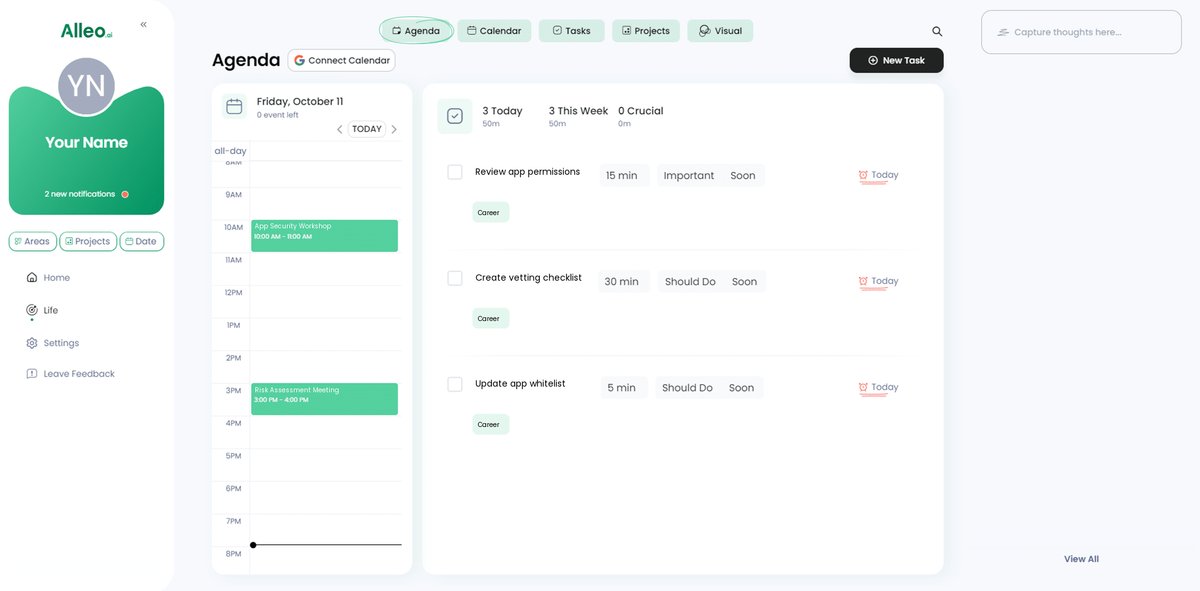
Bringing It All Together: Securing Your Workspace Apps
As we wrap up, it’s clear that evaluating workspace app security risks is crucial for protecting sensitive data. Taking proactive steps in IT security best practices can make all the difference.
You’ve learned about assessing risks, using a 5×5 matrix, and performing regular workspace application vulnerability assessments. Each step helps safeguard your organization’s cloud-based workspace security.
Remember, training users and monitoring app permissions are vital for data protection in collaborative apps. And automated security testing provides ongoing protection for mobile app security in enterprise environments.
Empathizing with your concerns as IT managers, I understand the challenges you face in cybersecurity for remote work environments. But with the right risk management strategies, you can effectively manage these risks.
Alleo is here to help, offering a personalized plan tailored to your needs, including user access control for workspace applications. Ready to secure your workspace apps? Try Alleo for free and get started today with evaluating workspace app security risks!